Admins may manage SSO providers for their organization in the Zunos Admin Portal. Both OAuth2.0/OpenID Connect and Saml2 are supported and can be configured.
Create SSO Provider
- Go to Settings > SSO > Add SSO
- Enter a name for the SSO Provider (this will be the name displayed on the login screen)
- Select the login method and click create
- Once created, the edit screen will be displayed with some generated fields that will be required when setting up the SSO integration with an external system. Users can also add a logo that will be displayed on the Zunos Login screen.
See below for some examples of how to setup an SSO integration with some popular authentication services.
Creating an App in Okta with OpenId Connect
This is a detailed walkthrough of how to create an SSO integration between Okta and your Zunos organisation. There is a similar tutorial created by Okta at https://developer.okta.com/docs/guides/build-sso-integration/openidconnect/create-your-app/. This walk through helps to provide additional information about what settings need to be configured in Zunos.
- Log into your Okta account. If you don’t have an account, signup at https://developer.okta.com/signup/
- Click Admin in the top right corner
- Switch to the classic UI
- Navigate to Applications
- Click ‘Add Application’ and then ‘Create New App’
- Set Platform to Web and ensure the Sign on method is OpenID Connect
- Click Create
- Add a name and optionally a Logo
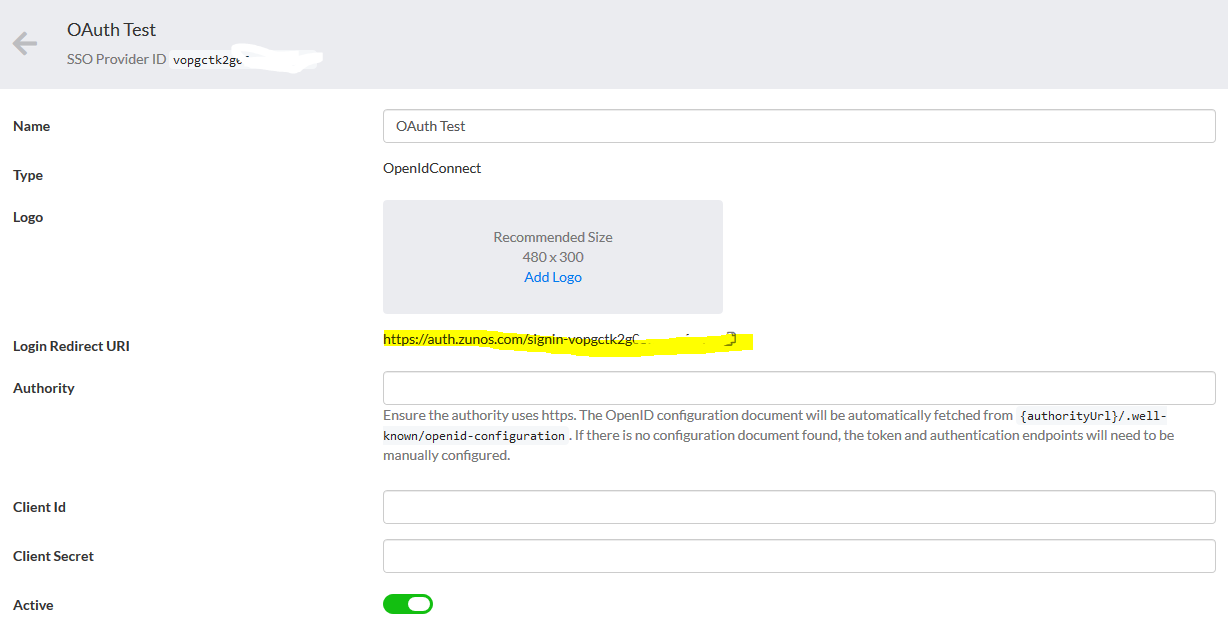
- Add a redirect Uri and click next. This can be copied from the Zunos Admin Portal in the “Login Redirect URI” field.
- Users will be presented with a screen that has Client Id, Client Secret, and a Okta Domain:
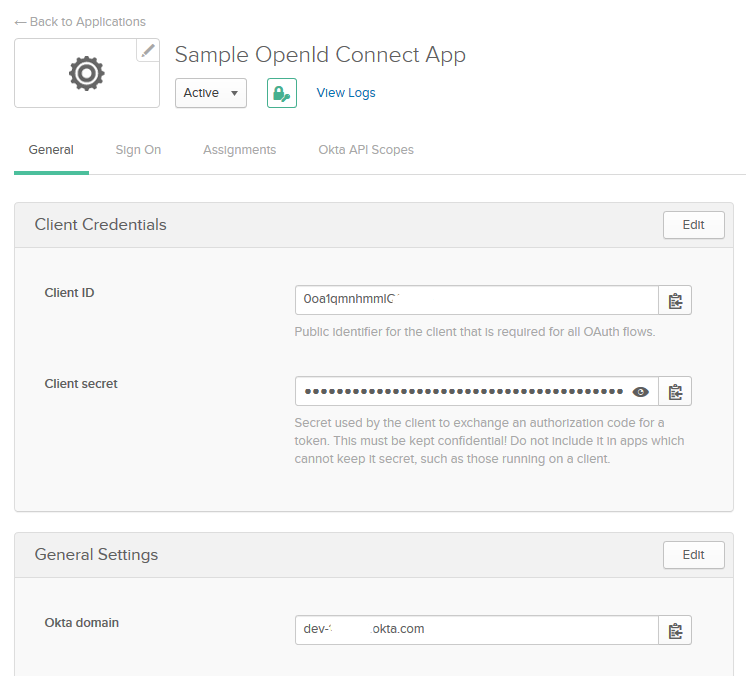
- Copy these fields and paste them into Zunos.
- In Zunos, ensure the SSO Provider in active and click save.
- Now, Users can test out the SSO provider when logging into either the Admin Portal or the Zunos Client Apps.
*Note: The Okta domain goes into the Authority field and needs to have "https://" added to the beginning.
*Note: If unable to log in via Okta SSO, try assigning the user to the application in Okta. Go to Your App Assignments > Assign > Assign to People and assign your user to the application.
Creating an App in Okta with Saml2
This is a detailed walkthrough of how to create an SSO integration between Okta and a user's Zunos organization. Visit: https://developer.okta.com/docs/guides/build-sso-integration/saml2/create-your-app/ for a similar tutorial. This guide provides insight on setting specifications when Creating an App in Okta wit Saml2:
- To begin, users must log into their Okta account. If you don’t have an account, signup at https://developer.okta.com/signup/
- Click Admin in the top right corner
- Switch to the classic UI
- Navigate to Applications
- Click ‘Add Application’ and then ‘Create New App’
- Set Platform to Web and ensure the Sign on method is SAML 2.0
- Click Create
- Add a name and optionally a Logo and click next.
- Add a Single sign on URL. This can be copied from Zunos Admin Portal
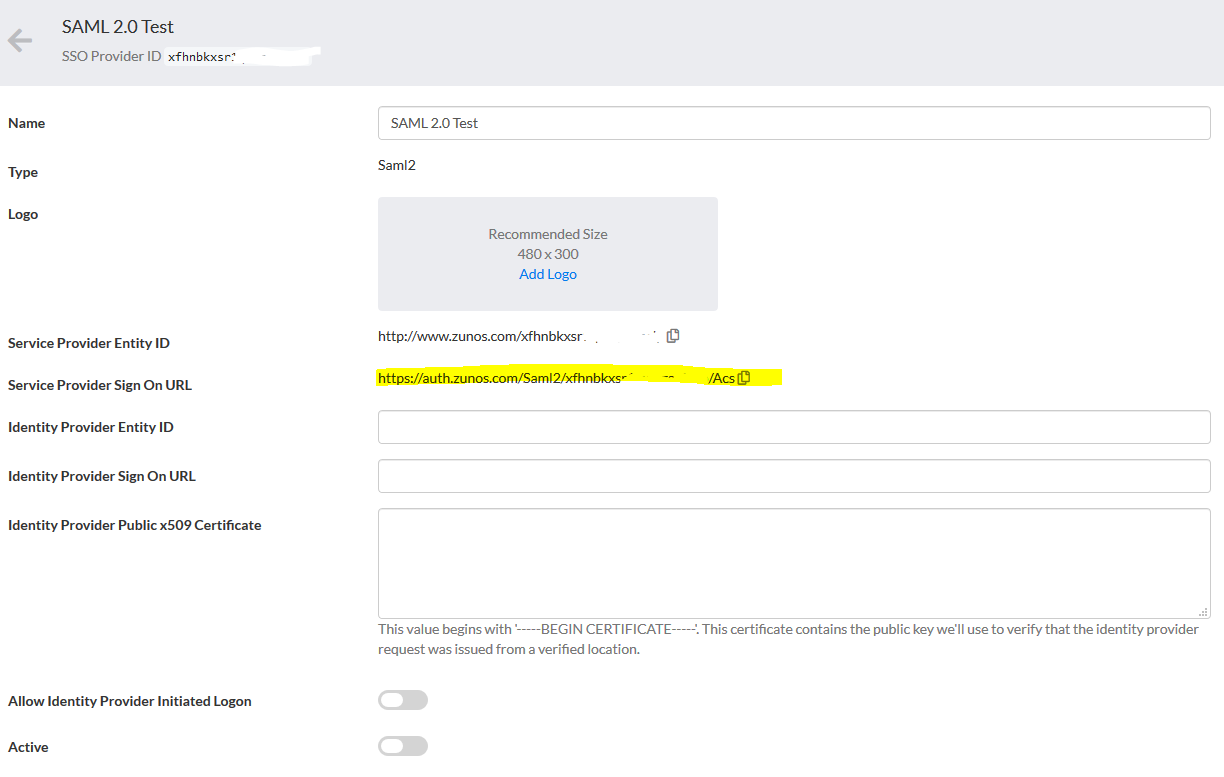
- Add the Audience URI (SP Entity ID). This can be copied from the Zunos Admin Portal
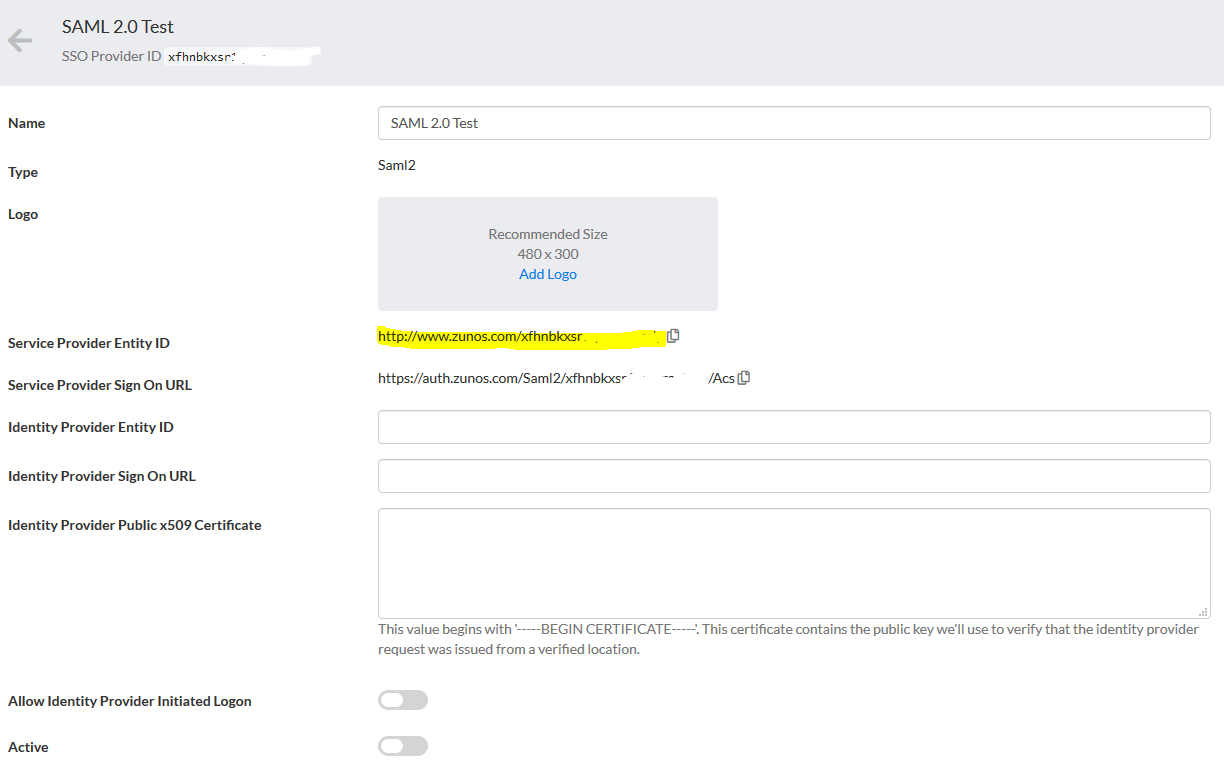
- If this App is just for testing purposes, select “I’m a software vendor” and click Finish.
- Click View Setup Instructions Click "Next"
- Copy the following fields and paste them into Zunos:
|
Okta Field |
Zunos Field |
Example |
|
|
Identity Provider Single Sign-On URL |
Identity Provider Sign On URL |
https://dev-13.okta.com/app/dev 13_samplesaml20app_1/exk1qf4x7/sso/saml |
|
|
Identity Provider Issuer |
Identity Provider Entity ID |
http://www.okta.com/exk1qmreaaEc4x7 |
|
|
X.509 Certificate |
|
-----BEGIN CERTIFICATE----- MIIDpDCCAoygAwIB AgIGAW+rgEQdMA0G CSqGSIb3DQEBCwUA MIGSMQswCQYDVQQG EwJVUzETMBEG A1UECAwKQ2FsaWZv cm5pYTEWMBQGA1UE BwwNU2FuIEZyYW5j aXNjbzENMAsGA1UE CgwET2t0YTEU MBIGA1UECwwLU1NP UHJvdmlkZXIxEzAR BgNVBAMMCmRldi0x MzQ5NzAxHDAaBgkq hkiG9w0BCQEW DWluZm9Ab2t0YS5j b20wHhcNMjAwMTE1 MjMxNzI3WhcNMzAw MTE1MjMxODI3WjCB kjELMAkGA1UE oeyGeryTYmLf1QPh tg3kaaWWQ5fAjJdT h7U4 /RRf+56MemKMJcHL 9Tn5Y0GMDqukow9n VQ48XwnF M0SU+ynSxevIZl4o 8kZAHQmJIqwrfOFY pNuJq5ACvS8MtXxK 8H6m0CxbZcO4aNrf CQN1rfn4pHm2 nv+qQaP2TSvGr8EH fDGqjNVSYfyQFIxj 9bPVSE7Nwu5MOdj6 4murtzn5ld9T0xy1 Ka7eoXdGb/IM +fgpkgxN8WX01tR1 PgDcVZVhN9nNzNsG -----END CERTIFICATE-----
|
15. Ensure the SSO Provider in active and click save.
16. Users should now be able to test out the SSO provider when you log into either the Admin Portal or the Zunos Client Apps.
*Note: If unable to log in via Okta SSO, try assigning the user to the application in Okta. Go toY our App Assignments > Assign > Assign to People and assign your user to the application.
Configure SAML 2.0 SSO provider from a metadata XML file
Often only a metadata document is shared when setting up an SSO provider. This document will look something like the following:
<md:EntityDescriptor entityID="http://www.okta.com/exk1qmrea"> <md:IDPSSODescriptor WantAuthnRequestsSigned="false"
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <md:KeyDescriptor use="signing">
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
MIIDpDCCAoygAwIBAgIGAW+rgEQdMA0GCSqGSIb3DQEBCwUAMIGSMQswCQYDVQQGEwJVUzET MBEG
A1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0 YTEU
MBIGA1UECwwLU1NPUHJvdmlkZXIxEzARBgNVBAMMCmRldi0xMzQ5NzAxHDAaBgkqhkiG9w0B CQEW
DWluZm9Ab2t0YS5jb20wHhcNMjAwMTE1MjMxNzI3WhcNMzAwMTE1MjMxODI3WjCBkjELMAkG A1UE
BhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lzY28xDTAL BgNV
BAoMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRMwEQYDVQQDDApkZXYtMTM0OTcwMRww GgYJ
KoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC AQEA
yt71xVT8fJptqOtyZTb+g+82U3IBxrCDAKvEnGTA2jZ6ZfI1JPLQX9Sf9rULQ2kZCt3mX4qy 1Cw+ OlphSF1UBKy7Fchn38Anya5twj8jCZPk2XDKUvuKv28MXqbTzc4WO
/k9t4zkhHch118MuhmsbVP0
H9Pb6p32N+oRRDOGAsUSXsnjAC1H2ziUcX+7pvIImSTQudazc
/Uch8UBS2HQJxuhrv2gUNi6w+XV bugjkRHp9GWAh+RxwBex14yrdpIw
/TDhcsjYtzugVpiljhnHhpHvurGJ5cEK82Owm7/4RbW4VrNe 6H
/fU1mHXQ96P+EpgJZv39LyPy4zATTRQ4i3YwIDAQABMA0GCSqGSIb3DQEBCwUAA4IBAQAhwh FH N5HgTwgmLKj9fx8WWR
/RHyZB6SnMLDFNu7+3sAHl5TKGUi2yhZx5bkTlOQppo3sjEeUVZ4jnpQUb oeyGeryTYmLf1QPhtg3kaaWWQ5fAjJdTh7U4
/RRf+56MemKMJcHL9Tn5Y0GMDqukow9nVQ48XwnF
M0SU+ynSxevIZl4o8kZAHQmJIqwrfOFYpNuJq5ACvS8MtXxK8H6m0CxbZcO4aNrfCQN1rfn4 pHm2 nv+qQaP2TSvGr8EH5MOdj64murtzn5ld9T0xy1Ka7eoXdGb/IM
+fgpkgxN8WX01tR1PgDcVZVhN9nNzNsG
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:NameIDFormat>
urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
</md:NameIDFormat>
<md:NameIDFormat>
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
</md:NameIDFormat>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings: HTTP-POST" Location="https://dev-134.okta.com/app/dev
13_samplesaml20app_1/exk1qmreaaEc/sso/saml"/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings: HTTP-Redirect" Location="https://dev-134.okta.com/app/dev
13_samplesaml20app_1/exk1qmre/sso/saml"/>
</md:IDPSSODescriptor>
</md:EntityDescriptor>
Currently Zunos does not automatically parse this document, so some of the values will need to be extracted and added to the SSO configuration in the Admin Portal. Below is the field mapping between the XML and Zunos.
|
XML Tag |
Zunos Field |
|
EntityDescriptor entityID |
Identity Provider Entity ID |
|
SingleSignOnService Location |
Identity Provider Sign On URL |
|
X509Certificate |
Identity Provider Public x509 Certificate |
Comments
0 comments